Summary
Like Zero Trust, Zero Data represents a paradigm that organizations can embrace to enhance their overall security posture. But the benefits go far beyond better security.

 A few weeks ago, I came across this article from StJohn Deakin from 2020 about zero data. I've been thinking a lot about zero trust lately, so the name leapt out at me. I immediately knew what StJohn was speaking about because I've been talking about it too. My new book, Learning Digital Identity, talks about the concept. But the name—zero data—is simply brilliant. I want to dig into zero data in this post. I'll discuss the link between zero data and zero trust in a future post.
A few weeks ago, I came across this article from StJohn Deakin from 2020 about zero data. I've been thinking a lot about zero trust lately, so the name leapt out at me. I immediately knew what StJohn was speaking about because I've been talking about it too. My new book, Learning Digital Identity, talks about the concept. But the name—zero data—is simply brilliant. I want to dig into zero data in this post. I'll discuss the link between zero data and zero trust in a future post.
StJohn describes the idea like this:
Personal data should be held by humans first, and by the companies, organisations and governments that humans choose to interact with, second. The ultimate in ‘data minimisation’ is for the platforms in the centre to simply facilitate the interactions and not hold any data at all. This is the exact opposite of our Google/Facebook/Amazon dominated world where all human data is being concentrated in a few global silos.
A zero data society doesn’t mean that data isn’t shared between us, quite the opposite. With increased trust and participation, the data available and needed to drive our global society will explode exponentially.
From The Future of Data is ‘Zero Data’
Referenced 2023-09-30T17:37:15-0600
If you think about this in the context of how the internet has worked for the last three decades, the concept of zero data might seem baffling. Yet, consider a day in your life. How often do you establish lasting relationships—and thus share detailed information about yourself—with every individual or entity you come across? Almost never. It would be absurd to think that every time you grab a coffee from the local store, you'd need to form a lasting bond with the coffee machine, the cashier, the credit card terminal, and other customers just to facilitate your purchase. Instead, we exchange only the essential information required, and relevant parties retain just the data that is needed long term.
To build a zero data infrastructure we need to transfer trustworthy data just-in-time. Verifiable credentials (VCs) offer a way to represent information so that its authenticity can be verified through cryptographic means. They can be thought of as digital attestations or proofs that are created by an issuer about a subject and are presented by the holder to a verifier as required.
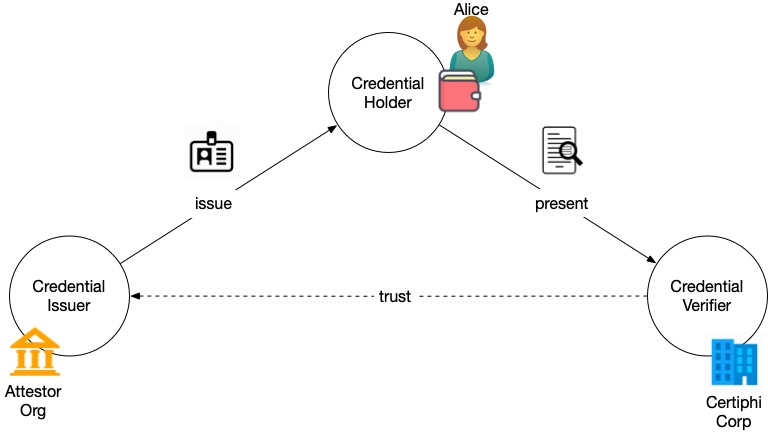
Here are some of the interaction patterns facilitated by verifiable credentials:
- Selective Disclosure: VCs enable users to share only specific parts of a credential. For instance, a user can prove they are of legal age without revealing their exact date of birth.
- Credential Chaining: Multiple credentials can be linked together, enabling more complex proofs and interactions. For example, an employer might hire an employee only after receiving a VC proving they graduated and another proving their right to work.
- Holder-Driven Data Exchange: Instead of organizations pulling data about users from third parties, VCs shift the interaction model to users pushing verifiable claims to organizations when needed.
- Anonymous Credential Proofs: VCs can be designed to be presented anonymously, allowing users to prove a claim about themselves without revealing their identity. For example, VCs can be used to prove the customer is a human with less friction than CAPTCHAs.
- Proofs without Data Transfer: Instead of transferring actual data, users can provide cryptographic proofs that they possess certain data or prove predicates about the data, reducing the exposure of personal information. For example, VCs can be used to prove that the subject is over 21 without revealing who the subject is or even their birthdate.
- Adaptive Authentication: Depending on the sensitivity of an online interaction, users can be prompted to provide VCs of varying levels of assurance, enhancing security in adaptable ways. I plan to talk about this more in my next post about zero data and zero trust.
These interaction patterns change traditional data management and verification models, enabling businesses to retain considerably less data on their clients. Verifiable credentials have numerous benefits and features of that provide a positive impact on data management, security, and user trust:
- Data Minimization: As we've seen, with VCs, users can prove facts without revealing detailed data. By selectively sharing parts of a credential, businesses only see necessary information, leading to overall reduced data storage and processing requirements.
- Reduced Redundancy & Data Management: Trustworthy VCs reduce the need for duplicate data, simplifying data management. There's less need to track, backup, and maintain excess data, reducing complexity and associated costs.
- Expiration, Revocation, & Freshness of Data: VCs can be designed with expiration dates and can be revocable. This ensures verifiers rely on up-to-date credentials rather than outdated data in long-term databases.
- Trust through Standardized Protocols: VCs, built on standardized protocols, enable a universal trust framework. Multiple businesses can thus trust and verify the same credential, benefiting from reduced integration burdens and ensuring less custom development.
- Enhanced Security & Reduced Exposure to Threats: Data minimization reduces the size of the so-called honey pot, reducing the attraction for cyber-attacks and, in the event of a breach, limit the potential damage, both in terms of data exposed and reputational harm.
- Compliance, Regulatory Benefits & Reduced Liability: Adhering to data minimization aligns with many regulations, reducing potential legal complications. Storing minimal data also decreases organizational liability and regulatory scrutiny.
- Cost Efficiency: By storing less data, organizations can achieve significant savings in storage infrastructure and IT operations, while also benefiting from focused data analytics.
- Enhanced User Trust & Reputation: By collecting only essential data, organizations can build trust with users, gaining a competitive edge in a privacy-conscious market that is increasingly growing tired of the abuses of surveillance capitalism.
In essence, verifiable credentials shift the paradigm from "data collection and storage" to "data verification and trust." This is what Marie Wallace means with her analogy between VCs and music streaming. Online interactions are provided with the assurance they need without the business incurring the overhead (and risk) of storing excessive customer data. Zero data strategies not only reduce the potential attack surface for cyber threats but also offers a variety of operational, financial, and compliance benefits.
The biggest objection to a zero data strategy is likely due to its decentralized nature. Troves of user data make people comfortable by giving them the illusion of ready access to the data they need, when they need it. The truth is that the data is often unverified and stale. Nevertheless, it is the prevailing mindset. Gettng used to just-in-time, trustworthy data requires changing attitudes about how we work online. But the advantages are compelling.
And, if your business model depends on selling data about your customers to others (or facilitating their use of this data in, say, an ad network) then giving up your store of data may threaten precious business models. But this isn't an issue for most businesses who just want to facilitate transactions with minimal friction.
Zero data aligns our online existence more closely with our real-world interactions, fostering new methods of communication while decreasing the challenges and risks associated with amassing, storing, and utilizing vast amounts of data. When your customers can prove things about themselves in real time, you'll see several benefits beyond just better security:
- Reduced Sign-Up Friction: For services that rely on verified attributes (e.g., age, membership status, qualifications), users can provide these attributes quickly with VCs, eliminating lengthy sign-up or verification processes.
- Cross-Platform Verification: A VC issued by one service can be verified and trusted by another, facilitating smoother cross-platform interactions and reducing the need for users to repetitively provide the same information.
- Fewer intermediaries: VCs can allow for direct trust between parties without the need for a centralized authority. This fosters more direct and decentralized interactions.
Zero data, facilitated by verifiable credentials, represents a pivotal transition in how digital identity is used in online interactions. By minimizing centralized data storage and emphasizing cryptographic verifiability, this approach aims to address the prevalent challenges in data management, security, and user trust. Allowing online interactions to more faithfully follow established patterns of transferring trust from the physical world, the model promotes just-in-time data exchanges and reduces unnecessary data storage. As both businesses and individual users grapple with the increasing complexities of digital interactions, the integration of verifiable credentials and a zero data framework stands out as a practical, friction-reducing, security-enhancing solution for the modern digital landscape.




